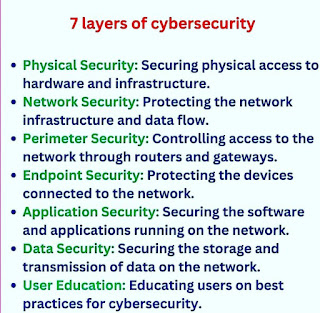
Here is a detailed overview of the layers of cybersecurity and some of the common tools used for each layer:
- Network Security: This layer involves protecting the organization's network from unauthorized access and cyber threats. Some of the tools used for network security include:
Firewall: A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
VPN: A virtual private network (VPN) allows users to securely access the organization's network from remote locations.
Intrusion Detection System (IDS): An IDS is a software application that monitors the network for any suspicious activity and alerts the IT team if any threats are detected.
- Application Security: This layer involves protecting the organization's applications from cyber threats. Some of the tools used for application security include:
Web Application Firewall (WAF): A WAF is a security system that monitors and filters HTTP traffic between a web application and the internet.
Vulnerability Scanners: Vulnerability scanners are automated tools that scan applications for vulnerabilities and provide recommendations for fixing them.
- Data Security: This layer involves protecting the organization's sensitive data from unauthorized access and theft. Some of the tools used for data security include:
Encryption: Encryption is the process of converting plain text into coded text to protect sensitive data from unauthorized access.
Access Control: Access control tools are used to manage user access to data and ensure that only authorized users have access to sensitive information.
Data Loss Prevention (DLP): DLP tools monitor data leaving the organization's network and prevent data leaks by blocking unauthorized access to sensitive data.
- Endpoint Security: This layer involves protecting the organization's endpoints, such as laptops, desktops, and mobile devices, from cyber threats. Some of the tools used for endpoint security include:
Antivirus Software: Antivirus software is used to detect and remove malware from endpoints.
Endpoint Detection and Response (EDR): EDR tools are used to detect and respond to cyber threats on endpoints.
Mobile Device Management (MDM): MDM tools are used to manage and secure mobile devices and prevent unauthorized access to corporate data.
- Cloud Security: This layer involves protecting the organization's data and applications in the cloud from cyber threats. Some of the tools used for cloud security include:
Cloud Access Security Broker (CASB): A CASB is a security system that provides visibility and control over cloud applications and data.
Cloud Security Posture Management (CSPM): CSPM tools are used to identify and remediate security risks in the cloud environment.
Cloud Workload Protection Platform (CWPP): CWPP tools are used to protect cloud workloads from cyber threats.
These are some of the common layers of cybersecurity and tools used for each layer. However, it's important to note that cybersecurity is a complex and constantly evolving field, and organizations may need to implement additional layers and tools depending on their specific needs and risks.

No comments:
Post a Comment
Thanks for your comments